2025년 회고
2025년은 정리보다 진행이 앞섰던 한 해였습니다. 연구와 일, 그리고 개인적인 사건들이 동시에 겹치면서 무엇을 이뤘는지보다 무엇을 미뤄두고 지나왔는지가 더 또렷하게 남았습니다. 이 글은 성과를 정리하기 위한 기록이 아니라, 한 해를 통과하며 쌓인 생각들을 미뤄둔 집청소를 하듯 하나씩 꺼내놓는 회고입니다.

On July 25th, 2023, EraLend suffered a 2.76M USD damage due to a Read-Only Reentrancy attack exploiting their collateral valuation algorithm. They are working to recover funds. SyncSwap, related in the attack, claims no responsibility. Impact on other zkSync Era protocols appears minimal.

EraLend is a decentralized lending protocol operating within the zkSync Era ecosystem. It is based on the well-known decentralized lending protocol, Compound V2, and functions similarly to Compound V2. In this incident analysis, we will briefly cover the Money Market, Comptroller, and Oracle, which are the main components of EraLend. Money Market is a form of bond created in the form of ERC20 tokens. When you deposit 1 ETH into the Money Market, you will receive a certain amount of tokens in return (referred to as cTokens in Compound and nTokens in EraLend). The exchange rate for these tokens fluctuates in real time based on various factors, including loan interest rates.
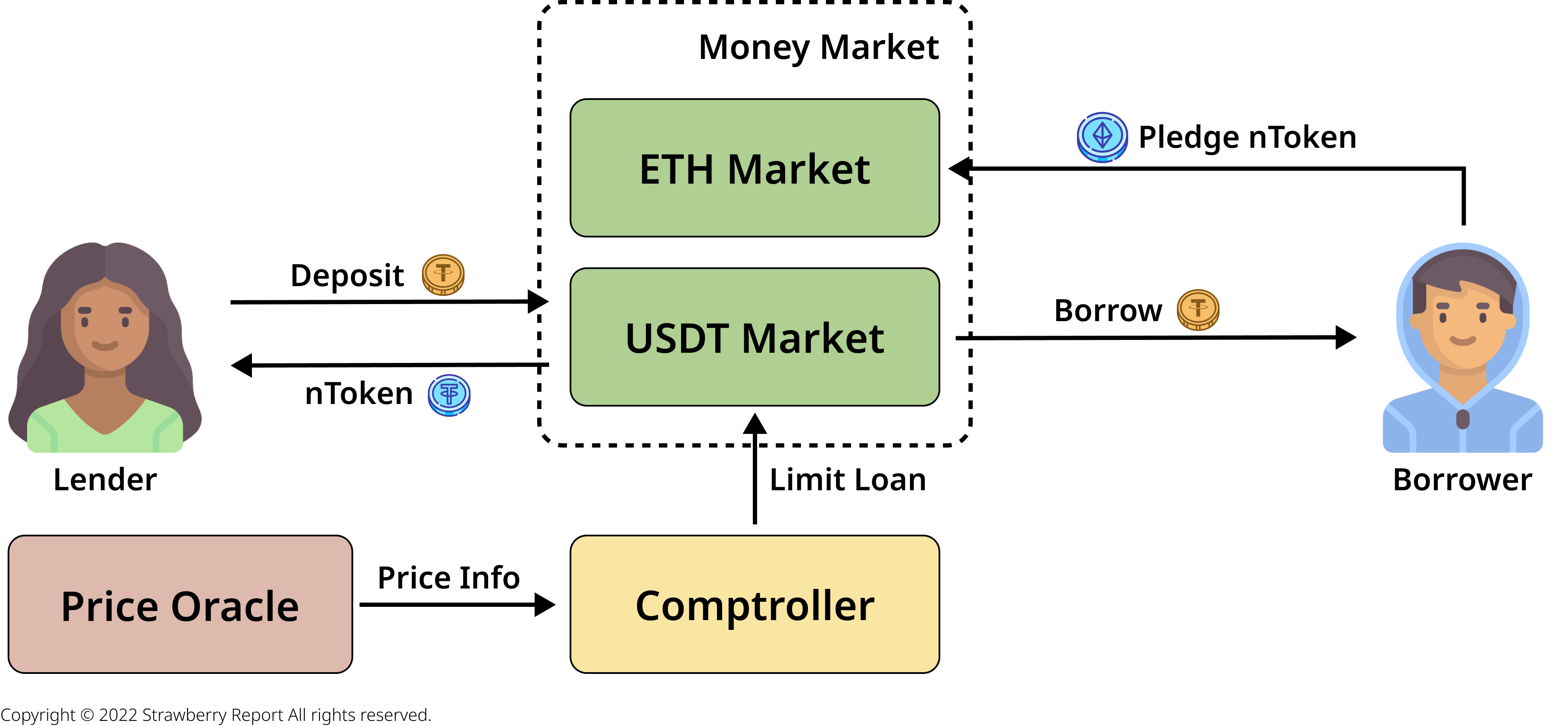
EraLend allows users to deposit a certain amount of nTokens as collateral and borrow nTokens based on the collateral ratio. For example, one could deposit 1 nETH as collateral and borrow 100 nUSDC. The Comptroller is responsible for assessing the eligibility for loans, and Oracle provides external price data to evaluate the values of different tokens. It's important to note that retrieving price information directly from decentralized exchanges is not recommended due to the risk of collateral price manipulation. In summary, EraLend is a decentralized lending protocol that issues debt tokens to create liquidity and connects lenders and borrowers through collateralized loans. You can refer to this article for a more detailed understanding of how EraLend and the Compound Protocol operate.
On July 25th, 2023, at 9:27 AM (UTC), two suspicious transactions occurred (Tx1, Tx2), exploiting the vulnerability in EraLend's collateral valuation algorithm. Velocore, SpaceFi, and SyncSwap used flash loans to perform the attack, resulting in approximately 2.76 million USD in damage.
The attack involves repeating cycles to gain profit. Here, we provide a simplified numerical view of a single attack cycle.
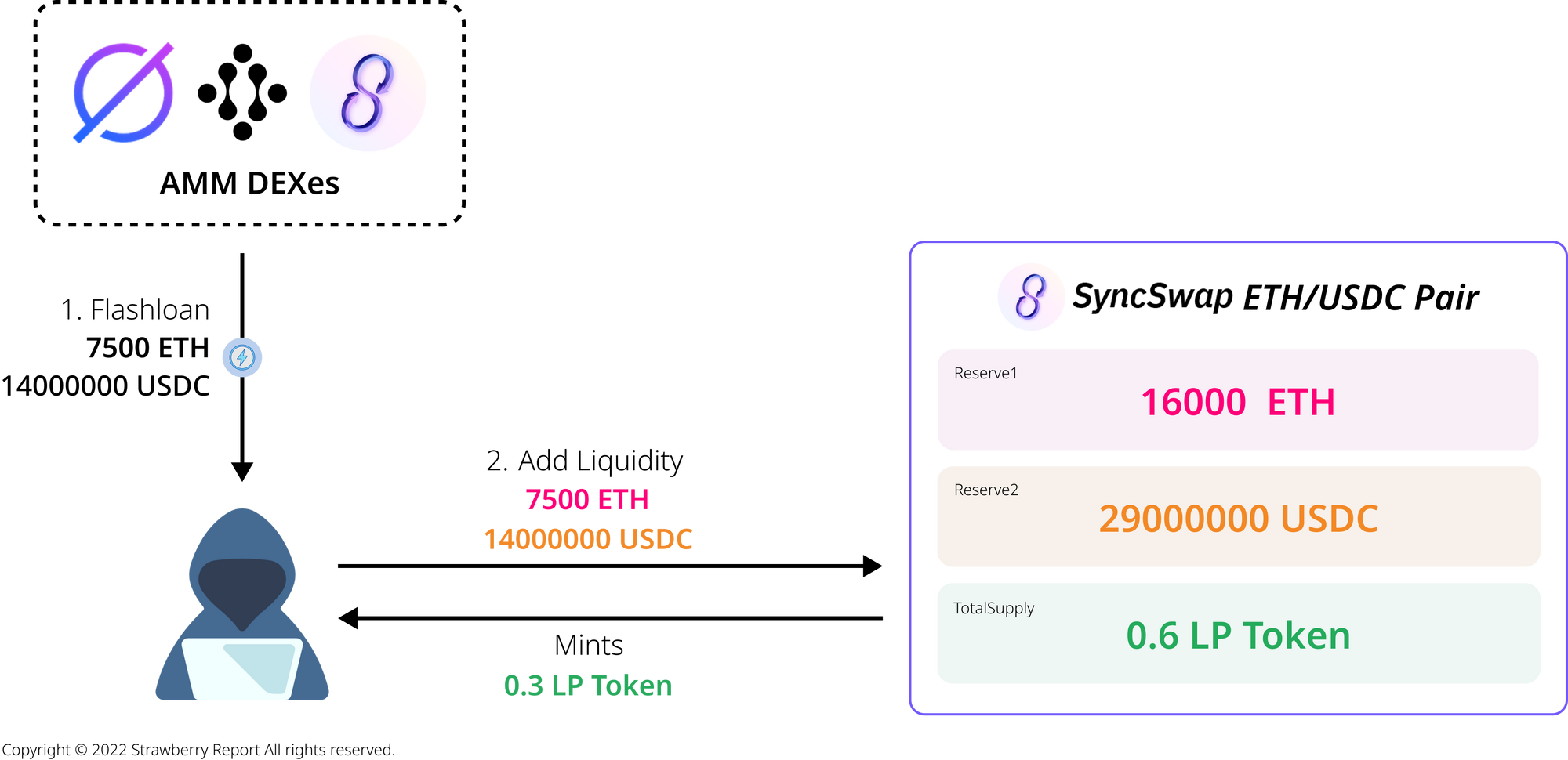
The attacker initially secures significant ETH and USDC by utilizing flash loans from various decentralized exchanges within the zkSync Era ecosystem. and then the attacker supplies liquidity to SyncSwap's ETH/USDC pair and receives 0.3 LP Tokens as a reward (exact figures may vary).
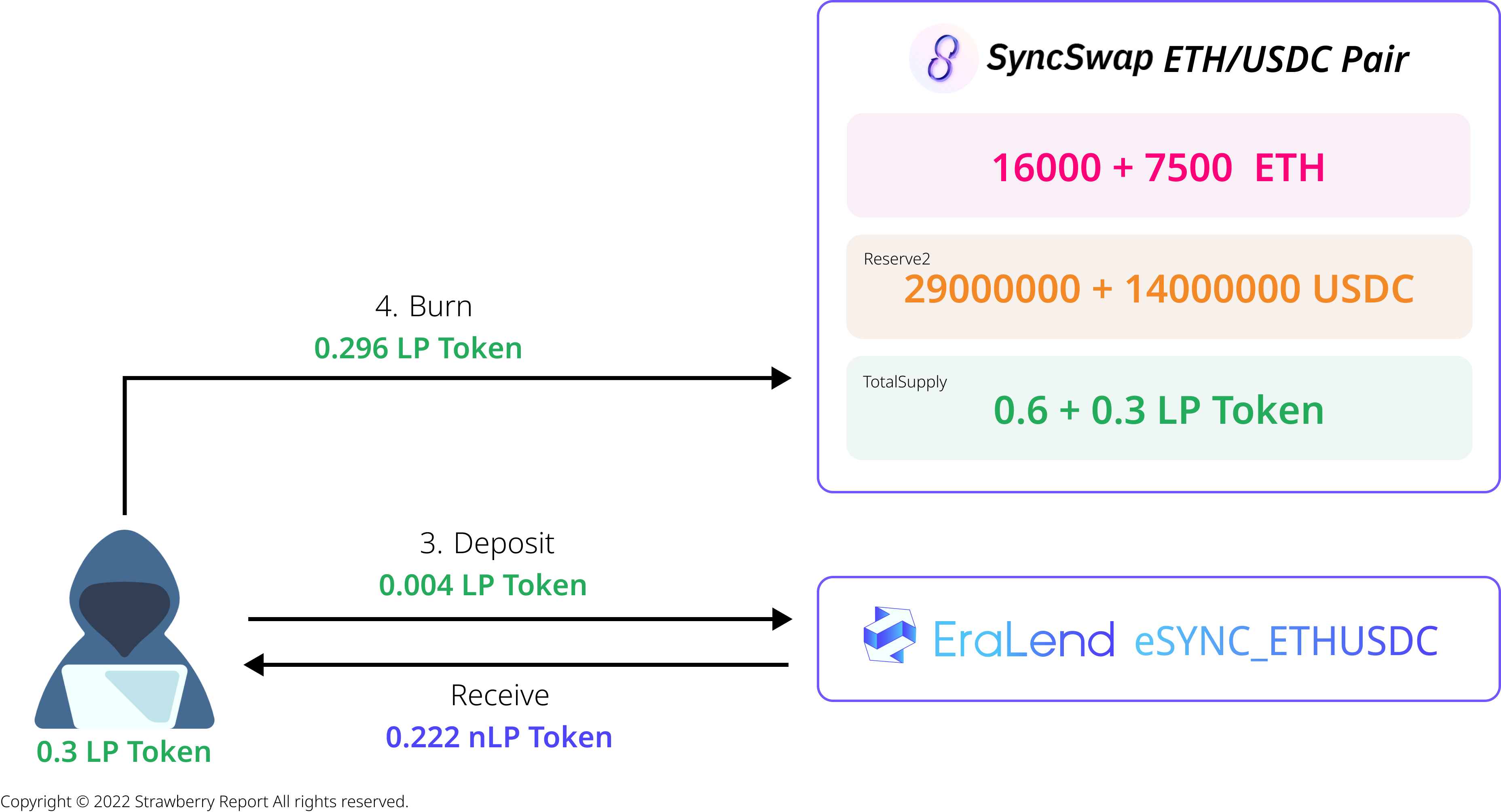
Next, the attacker deposits a very small portion of the obtained LP Tokens (0.004 LP Tokens) into EraLend eSYNC_ETHUSDC (consider it as nToken for LP Tokens) and receives 0.222 nLP Tokens. The attacker then burns all of their remaining 0.296 LP Tokens, specifying their self-made contract for the callback function.
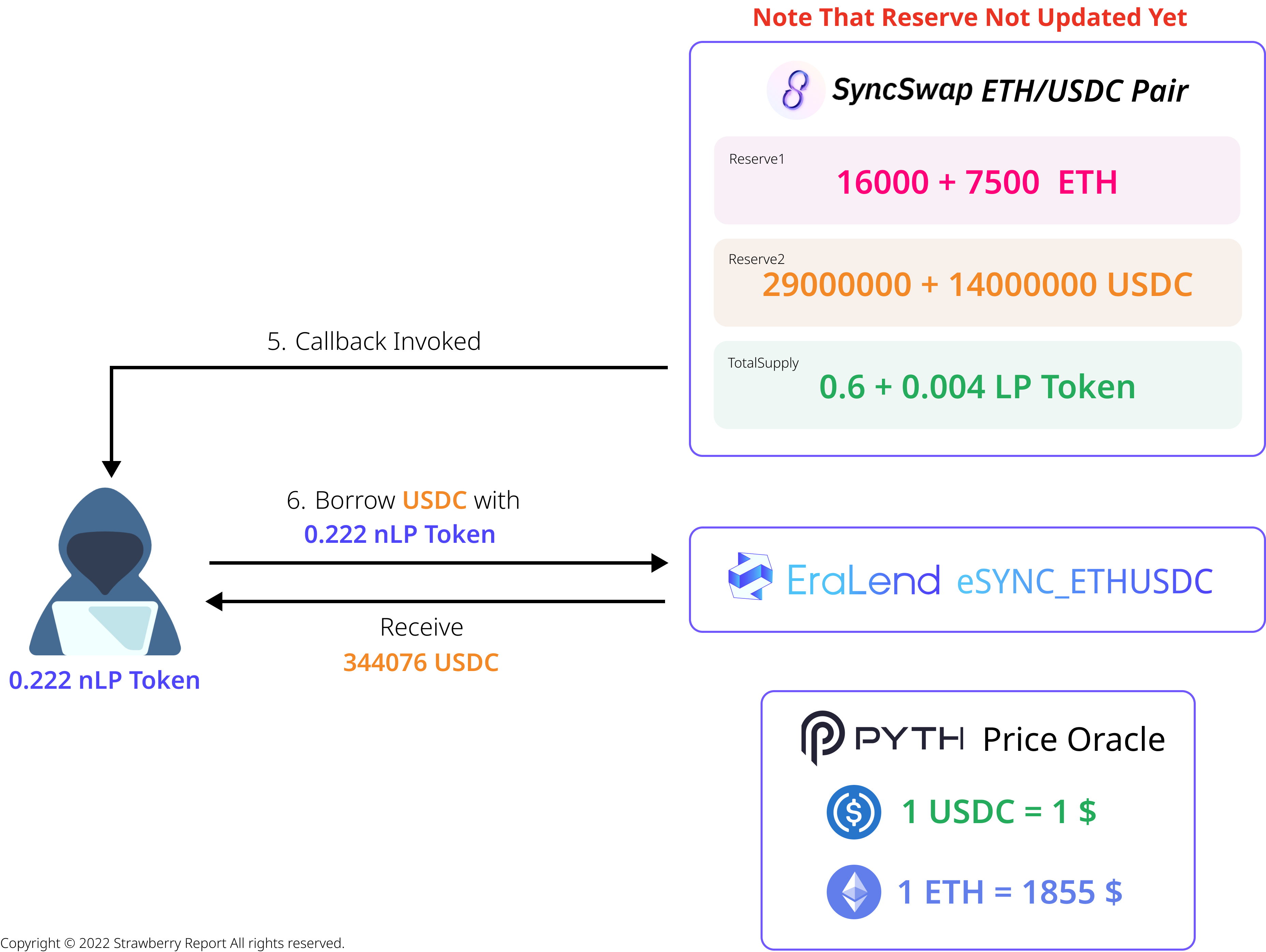
During the LP Token burning process, the callback is invoked. At this point, the update of reserve values, which represents the actual liquidity amount, has not updated yet. Taking advantage of this, the attacker executes a USDC loan by using their 0.222 nLP Tokens as collateral. EraLend calculates the LP Token's value using the Pyth Network's Price Feed and SyncSwap's Reserve Parameter.
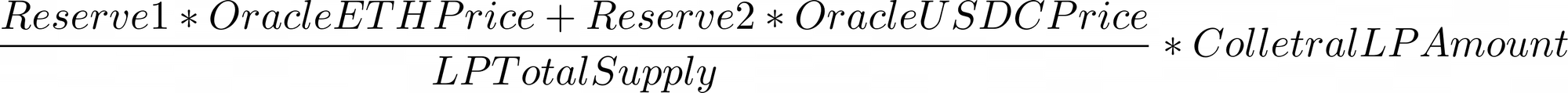
As the maximum loan allowed is 60% of the collateral value, the attacker receives a loan of 344,076 USDC.
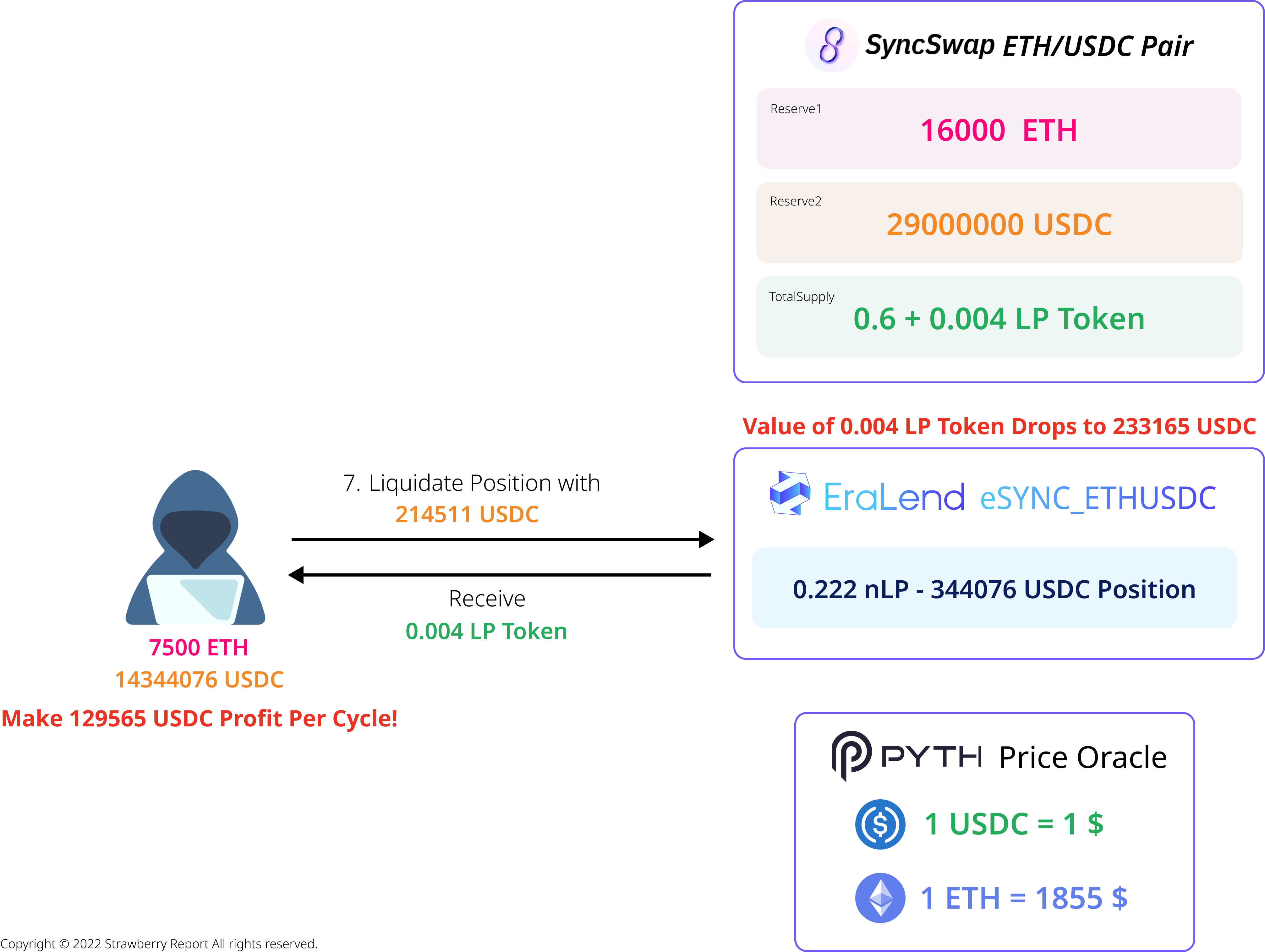
After the callback function ends and reserve values are updated, the LP Token's collateral value is recalculated to be 233,165 USDC, which becomes lower than the loan principal. In such a case, a liquidation process is triggered, where the liquidator can obtain the collateral by paying 92% of the current collateral value. Thus, the attacker pays 214,511 USDC to receive back their 0.004 LP Token as collateral. The attacker gains 129,565 USDC worth of profit in this single cycle, which is still a significant amount even after paying the flash loan interest. Moreover, the attacker can repeat this cycle until the balance of EraLend eSYNC_ETHUSDC is depleted.
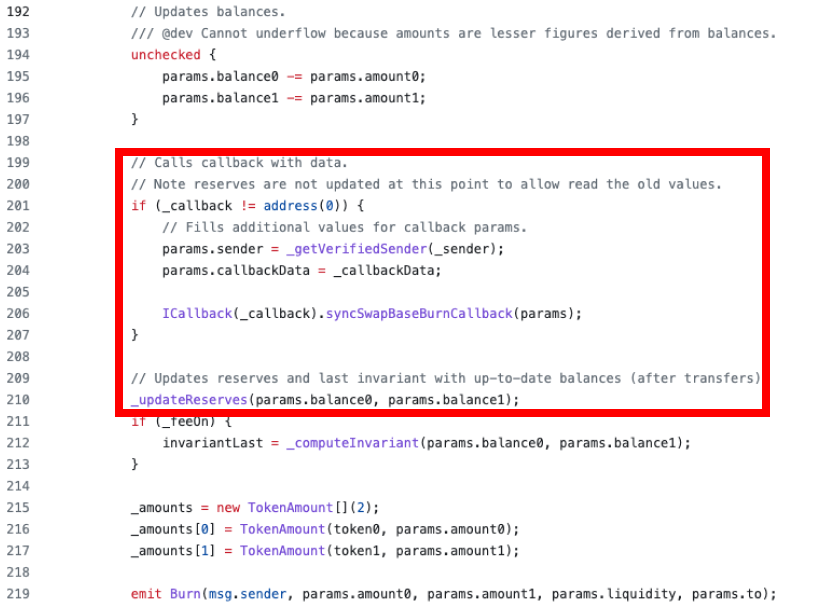
The root cause of this unfortunate incident lies in the position of the SyncSwap's callback function. The callback function is placed before the _updateReserves function at line 210, which allowed the callback function to manipulate the collateral evaluation based on reserve values.
The vulnerability that caused the EraLend incident is classified as Read-Only Reentrancy, where a point that relies on the state of an external contract can be called after the state has changed in the external contract. In this case, after the total supply of SyncSwap LP Tokens changes, the callback could call EraLend's borrow function, leading to Read-Only Reentrancy. To prevent reentrancy, a Check-Effect-Interaction pattern is commonly used, where critical actions, such as calling an external contract for a challenging verification process, are performed after updating most of the state. However, in the case of SyncSwap, the callback invocation at that specific location was intended design.
For a more detailed understanding of Read-Only Reentrancy, you can refer to this video.
After the incident, EraLend announced that they are actively collaborating with various individuals and companies to recover the funds and restore the service. (Twitter) They have suspended lending, USDC deposits, and LP Token deposits since the incident became known. EraLend has issued an open letter to the attacker, giving them until July 27th, 14:00 UTC, to return 90% of the funds; otherwise, EraLend will take all possible measures.
On the other hand, SyncSwap stated that they did not suffer any damages from the incident, and the callback implementation was intentional, so they bear no responsibility. (Twitter)
Since the zkSync Era ecosystem is still in its early stages and there aren't many protocols heavily relying on SyncSwap's state values, the impact on other protocols appears to be minimal.